LG Patches The SNAP Vulnerability In G3 Devices
From previous days so many problems are coming with LG phones but users need not to worry at least we know that fix/patches for them are ready. They have already patched a bootloop problem which enables to loose contacts which are in the versions of LG G4.
One of the South Korean Company found out the patches for a security hole in the LG G3. Almost ten million G3 phones are vulnerable to the malicious attacks by which their chat histories could be easily stolen.
LG researchers told that this problem is with the Smart Notice app(an app that shows notifications and suggestions on LG G3 phones). Along with that, this app also shows contacts, birthdays, and reminders so that we can easily be in a contact with other people. This app doesn't contain any kind of techniques by which users can check that data is valid or not, and that's why anyone can easily manipulate the data that contain some malicious code that allows an attacker to gain access to any information(may be public & private), data, photos and chat histories too. After being informed of the vulnerability, LG released the latest update to Smart Notice app.
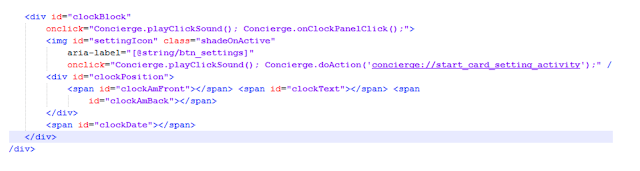
A "WebView"- based applications is used by Smart Notice app, The functionality of the "JavaScript" code is extended so that it enables the attacker to select from the biggest set of options. For this, we examined the client side application code, located in the following path: root/system/etc/mrg_default_forms/ConciergeBoard/.
We found two possible scenarios:
Use the Callback function (ConciergeBoard\card_forms\reconnect_noti):
Use the Birthday function (ConciergeBoard\card_forms\birthday_noti_contact):
The “@string” parameter displays the contact name without any validation, when a callback notification is set,
Further investigation revealed to us where the update process is found: (ConciergeBoard\default_view\container)
We have to find out that the “doAction” function is used as a JavaScript Interface which can easily communicate with “IurlActionHandler,” “setDbActionHandler,” “cardActionHandler” etc., obviously providing many sets of payload vectors to attackers.
We have to say "Thanks" to BugSec and Cynet researchers who have discovered such a malicious "severe security vulnerability" in LG phones. Researchers told the reason for it's severity that it lead to the authentic phishing attack and to fill the DOS on the device. While targeting this attack, an attacker run simple JavaScript code and it has a named too called 'SNAP'.
But, users need not worry the vulnerability is fixed now by the researchers. Now it's up to the owners of LG G3 to install the said update ASAP.
Watch "Snap" Vulnerability Video: