Row-bot/Robot Feeds on Rich Organic Matter in Dirty Water
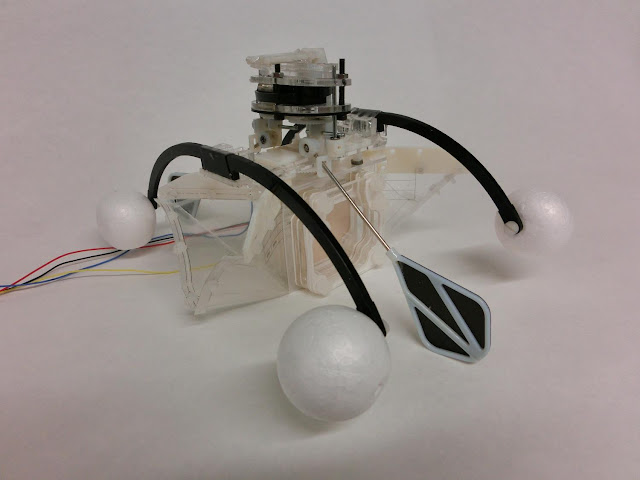
Swimming in the sea or a pool of polluted water could be unsafe though aquatic organism like water boatman would need the nutrients in polluted water to feed on. Researchers at the Bristol Robotics Laboratory – BRL have been motivation by the water beetles and other swimming insects and have developed the Row-bot, a type or a robot which tends to thrive in dirty water.
The Row-bot imitates the way the water boatman move and the way which it tends to feed on rich organic matter in the dirty water in which it swims. The purpose of the Row-bot project is focused to develop an autonomous swimming robot which is capable of operating indefinitely in remote unstructured areas by huntingits energy from the environment. When it tends to get hungry, the Row-bot opens it soft robotic mouth and rows forward to fill its microbial fuel cell – MFC, stomach with nutrient rich dirty water.
Thereafter it tends to close its mouth and the nutrients are gradually digested. The MFC stomach utilises the bio-degradation of organic substanceto generate electricity using bio-inspired mechanisms. When it has been recharged its electrical energy stores, the Row-bot then rows off to another new area for another drink of dirty water.
Row-bot – Environmental Clean-up Operation of Contaminants
The Row-bot had been developed at the Bristol Robotics Laboratory in collaboration between the University of Bristol and UWE Bristol by PhD student, Hemma Philamore together with her PhD supervisors, Professor Jonathan Rossiter from the University of Bristol’s Department of Engineering Mathematics and Professor Ioannis Ieropoulos from the Bristol Bio-Energy Centre at the University of the West of England. Professor of Robotics at the University of Bristol and BRL, Jonathan Rossiter informed that the work shows a vital step in the progress of autonomous robots with the potential of long-term self-power. Several of the robots tend to need re-charging or refuelling and often need human assistance.
A PhD student, Hemma Philamore stated that they anticipate Row-bot to be used in environmental clean-up operations of contaminants like oil spills as well as harmful algal bloom and also in long term autonomous environmental monitoring of harmful environments, for instance those which were hit by natural as well as man-made disasters.
Combination of Two Systems – Bio-Inspired Energy Source/Bio-Inspired Actuation
The sample robot combines two systems namely a bio-inspired energy source and bio-inspired actuation. While the first subsystem portrays the power generations potential of the robot, the second duplicate system begins the refuelling process, moving the robot with an energy needed which is less than the energy that is generated by the first system.
This has been achieved by feeding of the chemical energy contained in its surrounding liquid to support microbial metabolism within the MFC.Imitating the water boatman’s mechanism of feeding that works on a broad beaklike mouth to sweep in the liquid as well as suspended particulate matter, the Row-bot tends to feed its MFC stomach on opening and closing the mouth life orifice at each end of the MFC by bending of a flexible acetate envelope structure.
On utilising both of these systems, the robot tends to be totally independent in the water with the provision of enough energy available in the liquid.